
Could Artificial Intelligence Replace Human Doctors?
September 27, 2018How to Use Training to Make Sure Your Tech Team Is Keeping Up
October 4, 2018Everybody is talking about Virtual Private Networks, or VPNs now, but check if you are aware of all features and services this software provides.
Why Firewalls and VPNs Make Good Friends
Firewalls and VPNs complement each other by acting at different levels and resulting in a higher combined defensive power. While Firewall analyzes your incoming and outgoing data traffic and guards from viruses, VPN creates encrypted data exchange channels, hiding these from security threats (viruses, hackers, governments, etc.). By contrast to Firewall, VPN also hides your identity on the net, including the Internet Service Provider (ISP). Of course, your identity can be known to the VPN service provider, hence, the need to choose a responsible and acknowledged service, which has high standards and security practices.

If Hackers Attack, the VPN Server Will Take the Hit
Most people know that VPN ensures traffic protection by encrypting your connections. The fact that all communication goes through the VPN server means that when an attack on the IP address assigned to you by the VPN network happens, it is automatically directed at the VPN server, not at your primary IP address or device. Needless to say that the security systems installed on these servers are much more comprehensive and of higher quality than those of the average user. Thus, the VPN servers represent an important additional layer of protection for your Internet access, one which is valid for all your devices connected to the network.
The Vast Implications of Emulating Locations by VPNs
It is well-known that VPNs can be used to hide or emulate a different location and enable access to restricted media content. However, the implications of emulating another geolocation are far greater and often underappreciated. In particular, it is known that companies (e.g. hotel booking or airline ticket selling companies) might offer different prices to their customers in different countries based on certain marketing strategies/deals or the purchasing power of the population. A VPN allows one to take advantage of this.
Furthermore, many web-based services (e.g. plagiarism checking tools), websites (e.g. online news platforms), video streaming services, etc. restrict the amount of time or the number of services unregistered users can access for free. Hiding the identity each time allows the user to bypass these restrictions and maintain access to the products. Moreover, in many cases, these practices are not explicitly illegal. It is reasonable to assume that companies would adapt to the increasing abundance of anonymous users online, but it would take precious time, during which users would undoubtedly exploit these benefits.
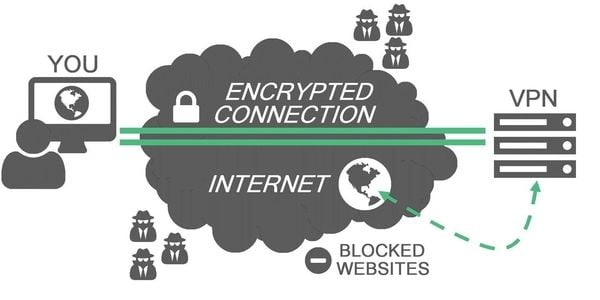
There are also examples when having control over your IP address makes your daily life easier by solving some inherent problems which many online platforms have. For instance, imagine you are traveling abroad and decide to make an online purchase from a certain retailer. In many cases, you’ll be directed at the website of the country of residence and switching to your native region or language might be very annoying and sometimes, even impossible. Now imagine on top, that you wanted to make a delivery to your original home location and another layer of difficulties and barriers pile up. Using a VPN helps you solve all these problems with a few clicks by choosing the geographic location of the server through which the data is routed.
The Vast Implications of Emulating Locations by VPNsMany VPN Services Log Sensitive Data, Which Can Be Hacked or Obtained by Governments
Talking about security standards, it is worth mentioning that many VPNs create and keep extensive logs for each of their users, hence, to eliminate the associated risk factors, some users prefer VPN services that do not save such logs or save as little sensitive information as possible. It might be an example of excessive concern (the data is most often intended for improving user experience), but we all know what powers governments have and what happens when they choose to put pressure on or “befriend” companies behind certain IT products, like antiviruses, messaging apps, etc. (especially the way it happens in some authoritarian regimes worldwide, which pass laws that require cooperation with the government).

Central national authorities indeed tend to dislike excessive privacy online. In fact, more than 10 countries worldwide have banned VPNs, while some are planning to do so. When this happens, it is very likely that the arguments being involved would be fighting terrorism or the fact that VPNs can be used for accessing restricted media content or P2P networks. When governments do decide to ban VPNs or forge the rules according to which these operate, obviously, no real privacy can be achieved, however, this is a rather extreme step.
VPNs Can Prevent Abuse by Your ISP and Increase Your Internet Access Speed
ISPs can interfere in your traffic in quite significant ways. For instance, they can see your searches, can intervene to add more adds and can use undetectable cookies (that one cannot delete) to track the HTTP traffic. Ultimately, they can even sell the data regarding your pattern of web access and user data to marketers (yes, this is legal in the USA). Finally, a lot of ISPs are known to split the data traffic into faster and slower “lanes” or throttle data traffic speed or bandwidth for certain websites. As stated by the Electronic Frontier Foundation, no regulation is preventing ISPs from doing these things, and there are many reported instances when these things happened.
Moreover, recent laws in the US gave more rights to ISPs effectively abolishing net neutrality – the principle according to which ISPs should treat all data traffic equally without discrimination according to users, websites, content, etc. by charging more or limiting access speed.
For now, VPNs can offer significant protection from the violations of ISPs and they can often result in higher Internet access speed due to the fact that encrypted communication does not allow ISPs to interfere in the data traffic. According to Ariel Hochstadt, the former marketing manager of Gmail, as soon as the Federal Communications Commission started working towards abolishing net neutrality in April 2017, there was a 170 percent increase in VPN sales. Some top companies selling VPN services registered increases in their pool of US customers of up to 250% in a year and representatives of these companies think that this increase was accelerated by the moves on dismantling net neutrality. In the face of this attack, VPNs allow users to retain their valued privacy.
To conclude, while many people tend to know what VPNs are, there are a lot more features to these both in terms of the security and freedom they offer to the user. Moreover, given the current realities, it is arguably also a form of political or ideological statement in favor of liberty.
3 Comments
Very informative blog. VPN is something not a can but a must these days. With all the internet connected devices we are linked, we got to have a vpn for security. I use PureVPN with addition of dedicated ip address for stability and better connection.
So true and informative. Thanks for sharing. The most common reason that gets proxies blocked is when a rate limit is not established beforehand. Web servers are designed to detect multiple activities such as login attempts that are done from one source in a short amount of time.
Thanks for sharing excellent informations. Your site is very cool. I’m impressed by the details that you have on this web site. It reveals how nicely you perceive this subject. Bookmarked this web page, will come back for extra articles. You, my friend, ROCK! I found just the info I already searched everywhere and just could not come across. What an ideal site