SSAE 18 Data Center Certifications (SOC I, II, III)
After completing a rigorous audit from a certified independent CPA, Colocation America is proud to have 22 SSAE 18 certified data centers operating in full compliance to the new SSAE 18 compliance standards. With this new certification, all servers hosted with Colocation America are secured through the implementation of IT controls that adhere to the new SSAE 18 compliant hosting guidelines.
Technicians working within the SSAE 18 data center facility operate according to a strict internal process to ensure that all servers are managed according. The new guidelines set forth by the American Institute of Certified Public Accountants (AICPA) are the standard that many colocation providers must comply with but many are unsure about SSAE 18.
There is much confusion as to which reporting standards a business should ask for from its data center service provider so here is a basic rundown for each type of SSAE 18 reports.
What Is SSAE 18?
The Statement on Standards for Attestation Engagements No. 16, or simply SSAE 18, is a set of guidelines for reporting on the level of controls at a service organization. The AICPA created the guidelines and went into effect May 1, 2017; replacing SSAE 16 which replaced SAS 70 as an auditing standard for service organization.
The new standard of reporting on internal controls of a service organization was drafted in order to update organizations in the US service industry to reporting standards that complies with the International Standard on Assurance Engagements No. 3402 (ISAE 3402).
There are two types of reports for SSAE 18 along with the addition of a new reporting framework, the Service Organization Control (SOC).
What Is SSAE 18 Type I and Type II?
An SSAE 18 Type I and Type II report is an effective way to communicate information about the controls a service organization has on its system. Both reports detail the opinion of an independent service auditor’s report on the organization’s system and the service organization’s description of the system.
However, any information provided by the independent auditor in regards to testing the service and its operating effectiveness are optional for a Type I report. A Type I report is geared towards service organizations that had not gone through a SAS 70 audit and would like to be set on its own path to a Type II reporting standard. The report covers the service organization’s controls of its system for a specific point in time.
A Type II report details the testing done on the service organization’s controls and its effectiveness. The audit usually last over a minimum period of six months which is stated in the report.
What Is SSAE 18 Compliance?
With the new framework of the SOC reports added to the SSAE 18 standards, SSAE 18 can now replace SAS 70 for service organizations to report on its internal business practices and system controls. The SOC reporting framework consists of 3 types of reporting standards; the SOC 1, SOC 2, and SOC 3.
SOC 1
SOC I reporting uses the SSAE 18 professional standard and is more geared towards reports on the Internal Control over Financial Reporting (ICFR).
It is designed to be a reporting standard for a business’ financial reports, highlighting its financial accounting and reporting practices. Although it is similar to the SAS 70 reports it is not relevant to service organizations like data centers which manage the IT infrastructure of multiple businesses.
SOC II
SOC 2 reports are unique to every organization. Each data center provider designs its own controls to comply with one or more of the 5 Trust Principles. SOC 2 is an internal report that gives all users how vital information about how this particular data center provider manages data.
There are two different types of SOC reports. Type 1 explains the provider’s systems and if their design can meet applicable trust principles. Type 2 specifies the operational efficiency of these particular systems.
A SOC 2 certification is done so by third-party auditors. These auditors assess the degree to how the data center provider complies with one or more of the 5 Trust Principles.
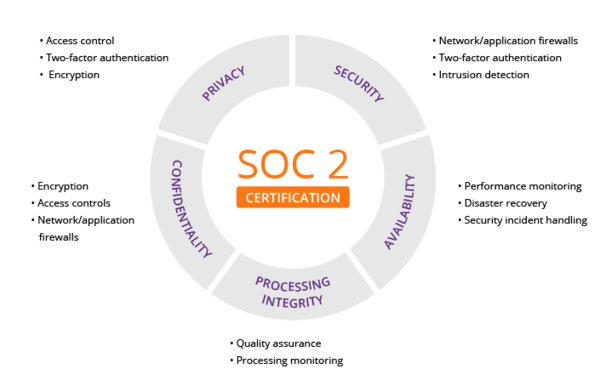
5 Trust Principles
Security – The first of the 5 Trust principles is security. This principle focuses on the protection of the system against unauthorized access. Access controls prevent possible abuse, theft, or unauthorized access and removal of data. It also covers the misuse of software and any inappropriate alteration or release of information.
IT security tools including two-factor authentication, web application firewalls, and intrusion detection can help prevent security breaches. It can also help data center providers with the first of the trust principles.
Availability – The second principle is availability. This indicates the accessibility of the system, products, and service. This is specified in the SLA (service level agreement), which is set by the data center provider and the user.
Processing integrity – The third of the trust principles is processing integrity. This assures that everything in the system is comprehensive, valid, accurate, timely, and authorized. Monitoring data processing along with quality assurance procedures helps safeguard processing integrity.
Note: If the data has errors before it was entered into the system. It isn’t typically the providers’ responsibility to detect.
Confidentiality – All personal or non-personal information data can be labeled as confidential. Once this information has been labeled as confidential, it needs to be protected as such. This will differ from one client to another. Encryption is important for safeguarding confidential data.
Privacy – The fifth and final trust principle is privacy. This principle covers the personal information that is collected, used, retained, disclosed, and disposed of to meet the entity’s objectives. As confidentiality can apply to various types of sensitive information, the privacy principle only applies to personal information.
SOC III
As with a SOC 2 report, a SOC 3 report also summarizes the information that is related to a service organization’s internal controls for security, availability, processing integrity, confidentiality, and privacy.
The primary difference between the two is SOC 2 is a restricted use report and SOC 3 is a general use report. It still provides the same attestation to the same information, but it doesn’t give specific details. This is also why it is more concise.
SOC 2 and SOC 3 are principally the same thing. The main difference between SOC 2 and SOC 3 is in the reporting. They differ in how the report is used and thus how detailed the reports are. SOC 3 reports are for general use that can be freely distributed to the public usually for marketing purposes.
Key differences between SOC 2 and SOC 3:
– While SOC 2 has two different types of reports, SOC 3 can only be done on the Type 2 examination.
– SOC 2 is a restricted use report. SOC 3 is a general use report that can be used by anyone.
– SOC 2 includes an independent auditors report. SOC 3 also has an independent auditors report but it is briefer.
– SOC 2 and SOC 3 both include a management assertion letter.
– SOC 2 has a complete description report. SOC 3 has limited details because it is for general use.
– SOC 2 has a complete listing of controls. SOC 3 does not include a listing of controls.
– SOC 2 includes the listing of tests of operational effectiveness. SOC 3 does not include a listing of tests of operational effectiveness.
In short, an SOC 1 report detail the controls over financial reporting of an organization while SOC 2 and SOC 3 reports are about the internal controls of the system that host the financial accounts and records of an organization.
Both SOC 2 and SOC 3 reports are more relevant for a business that are looking for a detailed reports over the internal controls a data center provider have set in place to protect against security breaches and prevention of data corruption.
Still Confused?
We here at Colocation America are ready to help you figure out your financial reporting needs. Corporations that abide by the Sarbanes-Oxley regulations will have to get a thorough understanding of the security practices put in place that protect their dedicated servers.
Figuring out which reports would provide the most relevant information is a key part in understanding the security of your sensitive business data. We will be happy to discuss with you and your auditor which type of reports you need to make sure that you (and us) stay in compliance with the operating standards of a good business.