
Mobile & Desktop Operating systems merging
June 29, 2012
Get the Most from Your Dedicated Server
July 3, 2012Data security is an ongoing concern for businesses of all sizes. Will the shift to Cloud computing increase the risk of compromise?
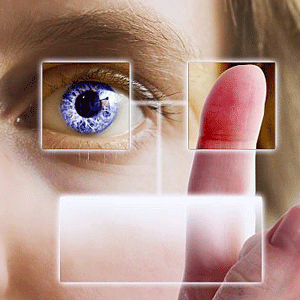
At the heart of cloud computing lies the promise of a no-strings-attached experience for the user. You can access your data from anywhere and everywhere if you’re on Cloud. But how safe that data is has been subject to some debate. The most recent effort to beef up data security is the bio-metrics recognition for Cloud by BioID; launched earlier this month for Intel SSO. It’s the first step to a whole new vision for Cloud security. And no this doesn’t mean you need to carry a finger print reader around with you -users can log on to their Clouds through any webcam available to them, be it a computer or a cell phone.
All Seeing Eyes
The hike in SaaS applications have resulted in some trouble for firms in terms of managing and creating a secure Cloud experience because of the excess in security approaches, identity stores, access policies, etc. Intel has been part of the solution so far which is why it’s no surprise that BioID started by developing biometric support for it first. Currently a simple webcam or camera phone can do the trick. BioID even made sure hackers can’t use a picture to gain unauthorized access to Cloud through “live detection”. Facial recognition won’t work if it doesn’t happen in real time.
Promising News
The idea sounds great when you think about it. Cloud computing at its best with secure access is a dream. Using someone else’s computer will no longer be a risk because a person wouldn’t be punching in their password at all. It is a high likelihood that systems fitted with key loggers for the purpose of monitoring someone’s activity will not be able to function properly. Computer monitoring activities will suffer somewhat because spyware or malware that acts by recording key strokes will be rendered useless. The user simply has to access Intel SSO for is/her identification to their cloud. Data stays safe and secure and away from intrusion by any key logger, spyware or malware.
Possible Kinks
Even though it’s another step in online security, there are a few problems that the BioID solution will not really do anything about. The very nature of Cloud computing makes it unsecured regardless of the creativity exhibited by BioID in making things more secure. Accessing Cloud on systems that don’t belong to the original user (including dedicated server hosting) is still a large risk which the biometric identification cannot manage to thwart no matter what it does. Granted that key loggers can do very little damage if they can’t record key strokes and ergo capture passwords, computers can still be fitted with spyware that captures browsing history. A hacker may not be able to gain access to someone’s password, but he can still see every single piece of information the Cloud user manages to browse through.
The Real Culprits
On a Wi-Fi network that has software such as Firesheep installed on it, the likelihood is that browsing data will be easily and effectively monitored and recorded; regardless of whether it’s a college, work place or local coffee house network. Then there are the more intrusive spyware and computer monitoring software that could exist on the system you’re using. Spector Pro 2011 and PC Pandora 7.0 are both examples of software that exist solely to collect data on computer usage. And because they run in stealth mode the likelihood is you won’t be able to find them to disable them or stop them from collecting your browsing data. Additionally, such spyware can also take screen shots of the browsing data it can’t record otherwise.
While it truly is a revolutionary step in Cloud computing, biometric identification will only go so far in keeping cyber criminals out of your data.
Author Bio Jane Andrew is a writer and guest blogger of mobistealth.com with years of experience in tech industry. She loves to write about cell phone spy software and computer and internet monitoring software. You can also follow her on Twitter @janeandrew01 to get tip and news about cell phone and computer security.

1 Comment
I think this should be done in the soonest time possible because of the privacy intrusions that have been happening owing to technology. I became a victim of one myself.