What Is Off-Shore Hosting?
April 15, 2020
SQL Server Backup Strategies
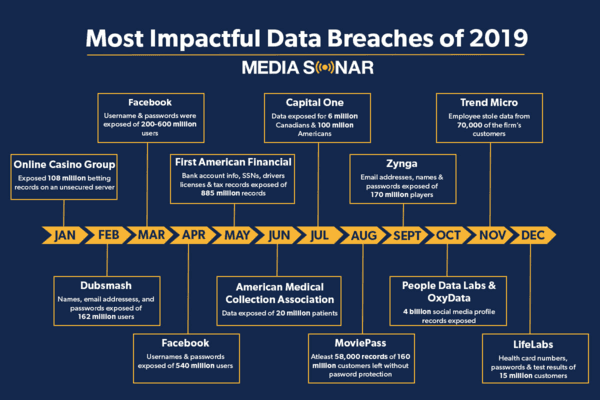
April 21, 20202019 was a landmark year in terms of global data breaches:
- Over 4 billion records exposed
- Almost 4,000 data breaches made public
- More than 50 percent increase in the number of reported breaches
No wonder spending on cybersecurity training is expected to reach $10 billion by 2027.
Technology is revolutionizing how the world works, especially how we manage data. The same can be said for cybercriminals who understand how sensitive online data is in the 21st century. These malicious entities are adopting new strategies and tools to access private information. As a result, the need for better security is rising by the minute!
Organizations looking to outsource work must ensure outsourcing agencies can protect their data. The good news is, 68 percent of outsourcing companies focus on data security while moving to the cloud. And it’s necessary given the vulnerabilities offshore teams introduce in business systems:
- Trojans or viruses embedded in software
- Penetration of offshore system defenses by hackers
- Unauthorized access by offshore personnel into parts of the client network
To overcome such data security issues, offshore teams should examine their security practices.
What Is Data Security?
Data security involves implementing standard controls, procedures, and policies to safeguard data against:
- Destruction
- Accidental loss
- Unauthorized access
Most organizations have some data security controls in place. Some are more robust than others. But they all prevent unauthorized disclosure or loss of valuable organizational data.
Proper data security benefits businesses by:
- Minimizing sensitive information leaks
- Building confidence among stakeholders and customers
- Preventing competitors from accessing future development and expansion plans
- Saving development and support costs
Data Security Challenges with Offshore Teams
Limitations in IT Technology
Almost 80 percent of cybersecurity attacks connected to offshore incidents are caused by human error. A lack of awareness training is to blame.
Many businesses combine in-house systems with wider networks. This helps facilitate faster information exchange between the IT and offshore teams. But it also creates vulnerable links within the system. Any cyber-attack may shut down the whole system.
Internet access among offshore teams for operational and leisure purposes sees numerous threats. The risk of cyberattacks is greater due to the dependencies of IT and offshore systems.
Also, the use of remote access from the IT domain to offshore teams comes with certain risks. If not properly controlled and monitored, the entire network attracts cybercriminals.
Quality of Work and Knowledge
Businesses subcontract to third-party agencies from low-wage countries. This reduces development costs. But cheaper services do not always mean higher profits, especially when offshoring.
Remember, low costs are synonymous with:
- Poor quality work
- Lack of technical capability
- Hidden costs
- Poor infrastructure
Time Zones and Cultural Differences
Communication is crucial when working with offshore agencies.
Ideas must be conveyed clearly and comprehensively for swift, efficient output. But communication is difficult when teams are miles and hours apart. Many businesses cannot keep up with the time difference. They cannot stay late every night to set a meeting with the offshore team.
Cultural differences are also prevalent. American culture, for example, differs from Asian culture. This increases the possibility of misunderstandings.

Companies and offshore teams may take separate approaches towards:
- Vulnerabilities
- Intrusion detection
- Perimeter defense
Discrepancies often create data security vulnerabilities for both parties.
What Are the Most Common Threats with Offshore Teams?
Risk of Network Breaches
Hackers and criminals can steal sensitive data. But not all hackers work from home and gain remote access to your work. Keep a list of all offshore employees with legitimate access to data. Can they abuse that privilege?
Consider disgruntled employees who might vandalize servers. Students or interns unknowingly exposing your data to malicious entities. Take the necessary precautions to prevent network breaches. Spare yourself a lot of heartache in the future.

Vulnerabilities in the network may cause operational disruption, financial loss, and reputational damage.
Disclosure or Leak of Intellectual Property
Your data security may be compromised due to opportunism or misunderstanding. Unscrupulous employees may work for you, but sell data to another. Or, they might release a copycat product.
IP theft is a legal issue. So, choose a reliable partner and ensure their vendors are reputable. Build precise language into the contracts to avoid any problems. If necessary, have them sign an NDA.
Sue the vendor, if a dispute arises. If you have the budget, retain an attorney in the country to act as your agent. Make him/her serve papers or make court appearances.
Physical Access to Unlocked Data
All your unlocked data is ripe for the taking. It’s worse if employees have physical access. Someone may physically break into your office and steal your data.
Discuss the vulnerability in detail with your offshore development team. Get ready to take action if any attempt occurs. Do a quick audit of your systems for unlocked data and set privileges.
What Are the 5 Precautions to Ensure Data Security?
Secure Network Monitoring
Set up a secure network. Focus on configuration management of expanding, ever-changing networks. Offshore teams should isolate and update networks connected to each client system.
Strengthen your offshore IT security:
- Train employees in cybersecurity principles
- Install, use, and update antispyware and antivirus software
- Use Internet firewall
- Download and install OS and application software updates
- Create backups of valuable business data
- Control physical access to network components and computers
- Secure Wi-Fi networks
- Change passwords regularly
Establish a Notifiable Data Breach (NDB) Scheme
Take inspiration from the Australian Government. Devise your own NDB scheme that triggers notifications and the cost of compliance. This will help you overcome offshore issues:
- Under and Delayed Reporting
The number of records exposed increased by 284 percent compared to 2018. But under-reporting may still pose a problem. Businesses may try to reduce potential damages by not making data breach incidents public. Delays may also exist in reporting or covering up incidents deliberately.
Unethical Solutions for Affected Individuals
Offshore teams might not notify data subjects affected by a breach. Instead, they might consider prompt remedial actions. This includes changing passwords or canceling credit cards. Early notification helps you minimize or avoid damages later.
- Poor Compliance
Offshore teams require a mandatory system in place. Only then will they reconsider what personal information to collect. Also, deliberate the period for retaining the data. Poor compliance can hamper your business’ reputation.
- Uneven Playing Field
Without a universally agreed set of best practices, a level playing field is impossible for businesses. They will constantly suffer inconsistencies when handling data breaches. At the same time, your IP becomes a target for hackers and cybercriminals.
No Remote Access to Sensitive Data
Remote working conditions increase the possibility of theft and malfunction. So, work at a particular site. Avoid risks by:
- Develop a separate repository for your offshore team. Put only the information necessary for completing tasks. Ensure the offshore team notifies you before accessing any information.
- Do not provide access to other company data. Monitor additional activities.
- Organize different levels of employee access within the offshore team.
- Encourage a culture of responsibility among offshore staff. Each worker should take responsibility for his/her actions.
- Relocate offshore specialists to your office when dealing with sensitive data. This helps you control all processes and communicate directly.
Human error can dismantle strong security procedures. The worst part is, you cannot fully account for human error. But do your best to contain its potential in a controlled environment. Implementing a policy that does not allow sensitive data to leave sight of your security personnel is a good way to do so.
Issue dedicated laptops and devices for business use. Make sure they do not leave the office unless urgent. Ramp up your security by avoiding:
- External hard drives
- Unauthorized cloud storage services
- Flash drives
Make it clear that the policy protects the whole company. Convey the penalties for violating the same.
Enable Two-Step Authentication System
The multi-factor authentication market will grow to $18.5 billion by 2025. And with good reason.

Two-step authentication techniques have grown rapidly among businesses. It is a must-have if you’re working with an offshore team. This method uses basic unique individual identification factors. You can easily authenticate and secure end users.
Depending on the project needs, you might share payment data. Or, you provide access to employees across platforms. Whatever the case, ensure your data is in safe hands. Two-step authentication helps you control and track who sees what business data.
Monitor Your Database Activity
Ask your offshore team the right questions. Especially if the project involves sensitive user data, ensure developers take security seriously.
Your preferred offshore team should have:
- Active network monitoring to detect breaches
- Enterprise-grade firewalls
- Regular security audits
- In-house IT policies for file sharing and messaging
Frequent checks are necessary, so your policies can meet current challenges. Record actions and data movement so you know how information is handled. Also, keep track of how employees access what data and when.
Have a complete history of all your transactions in one place. Use the information to determine data access and modification patterns. Avoid information leaks and control fraudulent changes. What’s more, inculcating these habits in offshore teams helps detect suspicious activity in real-time.
Remember – a chain is only as strong as its weakest link!
Your business may be tempted to skimp on security at offshore locations. But that puts your entire operation at risk. In fact, set stricter security controls than for doing the task in-house. Secure your offshore team and protect valuable customer data. This is the best way to avoid becoming a cybersecurity headline!