
8 High-Tech Trends That Are Revolutionizing SEO
September 19, 2018
What is Mesh Networking and Why You Should Consider it
September 26, 2018Cyber attacks are nothing new, but the latest round of attacks has bamboozled the digital world. Hundreds of thousands of devices have been affected by the recent malware attacks. Usually, these types of threats used to be mainly targeting corporate devices, but that’s not the case anymore. Now, pretty much everyone is at risk. Many digital users have neglected the aspect of cyber security for so long. They’re slowly realizing the importance of it. If you’re still among such people who don’t take the digital security seriously, you should definitely know about the latest attacks that have targeted loads of devices all around the world.
Biggest Malware Threats That Have Attacked Users in the Recent Times
In order to protect yourself from the danger, you must first know the extremity of the danger itself. Continue reading to find out the latest and dangerous malicious threats:
- WannaCry: Of course, the first mentioned would be about the most-hyped cyber attacks in the recent times. This is a ransomware attack module, where these malicious worms are deployed into the victims’ devices through different types of doorways, mostly through phishing emails. Once deployed, these worms encrypt the local files and allow the user to get back their data only after paying the demanded ransom. Although, most of these attacks are directed towards organizations and business networks, there were still several instances where many common people have fallen victim to WannaCry attacks. Furthermore, these attacks also target the computers with mainly outdated software.
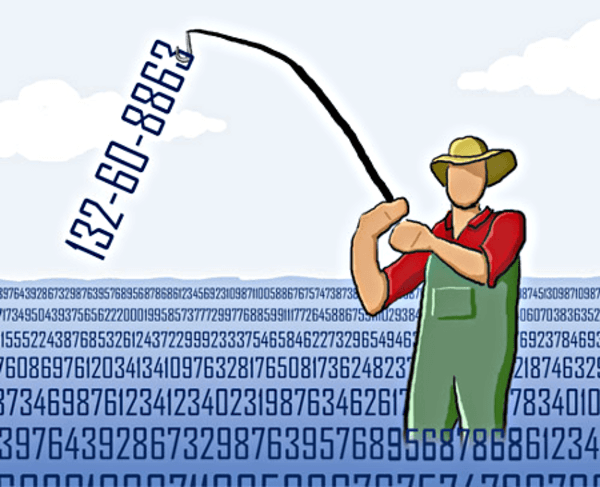
Image Source: techworld
- Loyphish: This is basically a phishing page which disguises as a legitimate banking website. These webpages are highly sophisticated in design, which makes you believe that you’re interacting with the original website of your bank. These pages are cleverly built with all the original images, logos, and text. These attacks are targeted against pretty much everyone. So, if you ever enter your banking info into any of these pages, you may lose substantial amounts of money. Usually, malware phishing pages can be avoided by double-checking the URL of the page in your browser’s address bar. Also, using an Internet Security tool can help you by leaps and bounds in avoiding such threats.
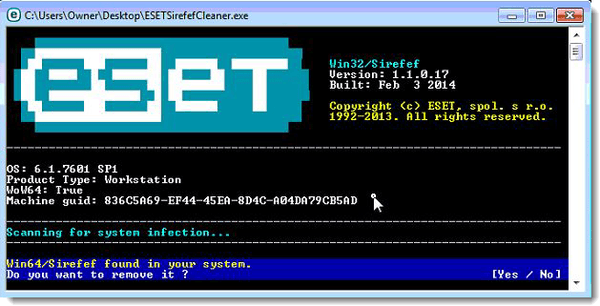
Image Source: vir.us
- Sirefef: This is one of the most advanced malware threats out there. Many devices have been affected by this in the recent times. Also known as ZeroAccess, this malicious threat operates in complete stealth mode, leaving little to no trace of its existence in your device. Furthermore, it also has the capability of disabling the security defenses of your computer. This file usually gets into your device when you’re downloading pirated files, software, and similar others. So, if you’re downloading cracked software or keygens, you could be making your computer vulnerable. Sirefef also transmits your confidential information to remote servers. Additionally, it can also disable your Windows Firewall and Windows Defender as well.
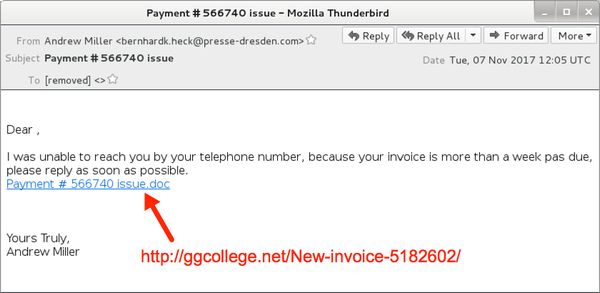
Image Source: eset
- Emotet: Here comes one of the most dangerous and savage malware threats we ever know. Emotet is a sophisticated Trojan, which spreads at an exponential rate, affecting more and more devices. This infection may come in different forms such as pdf files, word documents, suspicious links, and many more. If you ever download a file from unknown sources intentionally or unintentionally, you’re doing harm to your own self. This malware can easily wipe out your bank account in seconds. Recently, this Trojan has evolved into a new form, where it can also act as a distributor for other malicious threats.
- Suspicious.Emit: This is a Trojan malware that can do a serious harm to your computer. Usually, Trojan horses are seriously malicious files that disguise themselves as useful applications such as utility tools. Suspicious.Emit is among such Trojan threats, which could present disastrous damage to your device. It operates through code injection technique, where it gains immunity from detection. Along with that, it also creates an autorun.inf file and places it in the root directory of the victim’s device. This type of threat is usually deployed through removable devices such as USB drives. Suspicious.Emit also has the ability to steal your information and transmits to other devices and servers.
- FBI Virus: A highly dangerous malware, FBI virus which is alternatively known as FBI Moneypack Scam, is a very cleverly designed malicious file. When attacked by this threat, your computer will display an alert which states that your computer has been locked down due to violations of copyrights. This alert tries to deceive you that you’ve been blocked due to any type of illegal access or downloads of files such as music, software, movies, and many others. In order to get your computer unblocked, you would have to pay two hundred dollars. Many commoners have fallen victim to this scam, making it one of the hazardous attacks in the recent past.
- Zbot: A Trojan malware that has affected thousands of devices for a long time, Zbot has been labeled as one of the ruthless malicious attacks in the recent era. Also known as ZeuS, it uses form grabbing and keylogging to steal your banking credentials. By doing so, it gains the ability to track your financial information steal your money from your bank accounts. One of the highly bothering aspects of this threat is, it’s very difficult to identify this Trojan malware. Using the top-rated anti-malware programs is the only way to detect and remove this Trojan from your device.
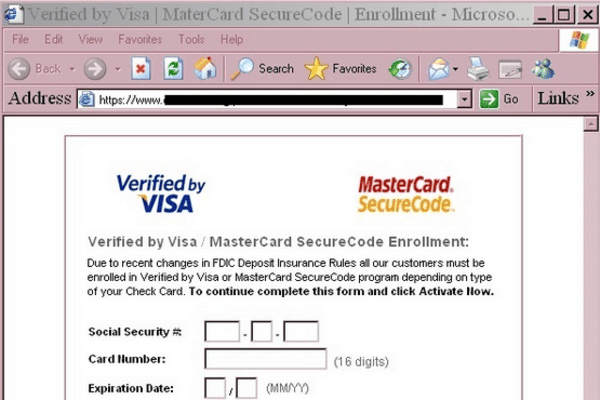
Image Source: techpp
Conclusion
By now, you may have gotten a deep insight into some of the highly dangerous malware threats that have attacked and affected thousands of devices in the recent times. If you want to safeguard yourself from such attacks, you must tighten up your security defenses by using a good anti-virus program that offers an effective combat system against malware threats.
